This guide does not dive into specific authentication methods, see Authentication
Methods for more details on the different methods available.
Connectors
Connectors are the starting point in how Versori provides integrations to external systems. Unlike other iPaaS‘s, Versori does not rely on “pre-built” connectors, we use AI to generate Connectors driven by the context of the users requirements given in either Plan or Build.How Connectors Work
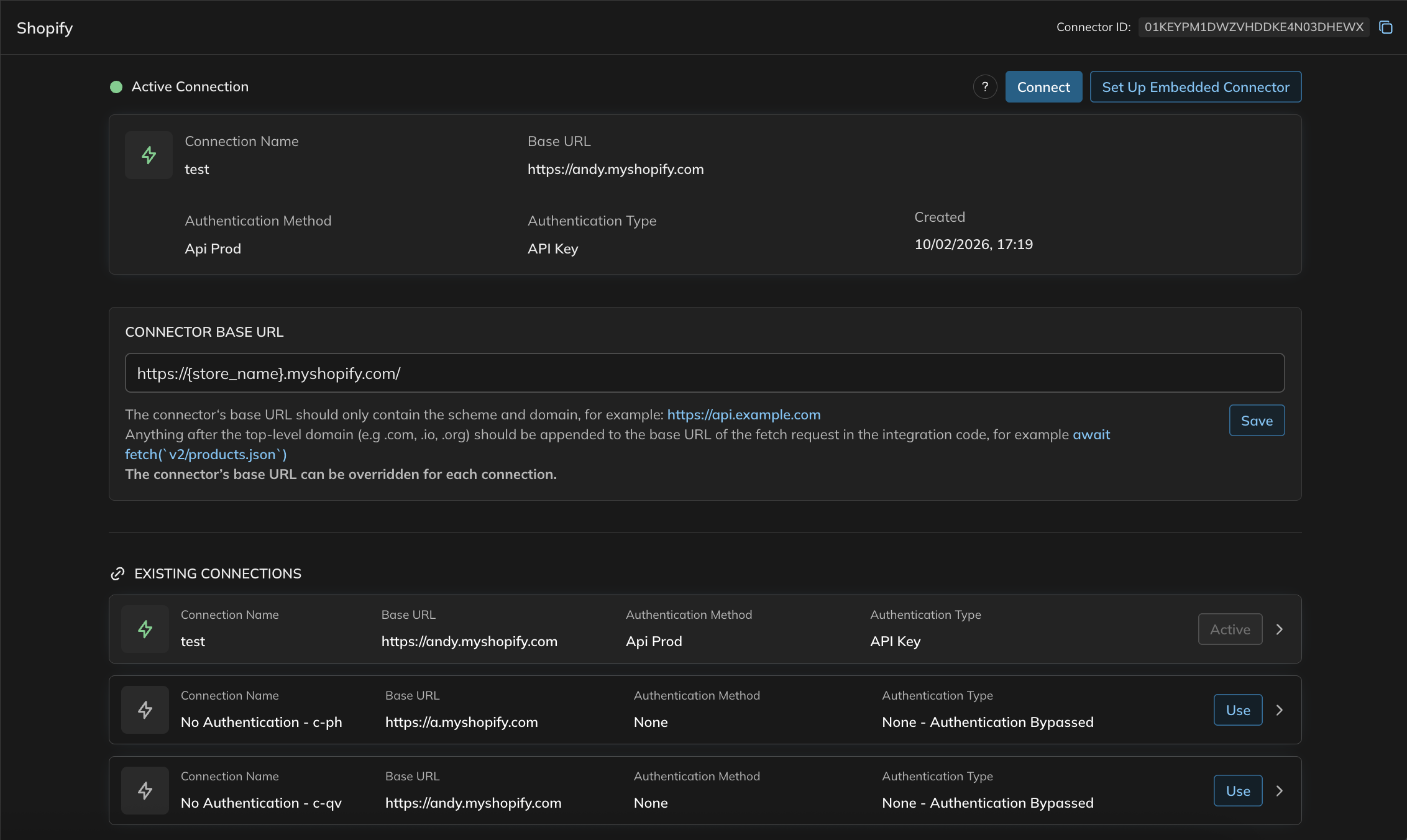
When you use a connector for the first time, Versori creates a central version of it behind the scenes. This acts as the main connector. Each time you use that connector in an integration, a linked version is created specifically for that integration. We call this a connection template. This setup allows you to reuse the same connector across multiple integrations without having to recreate it each time.Connecting Once, Using Everywhere
When you connect to a connector, your connection is linked to the main (central) version. This means you only need to enter your credentials once — even if you use the same connector in many different integrations. For example, if you use the same connector in 100 integrations, you won’t need to authenticate 100 times.Authentication Made Simple
Each connector supports specific authentication methods (such as OAuth or API keys). Versori supports the most common industry-standard authentication types by default. Authentication options are managed centrally, so they’re available wherever the connector is used. When you create a connection, your chosen authentication details are securely saved with that connection. Even if authentication settings are later updated or changed, your existing connections will continue to work as expected.Managing Connectors
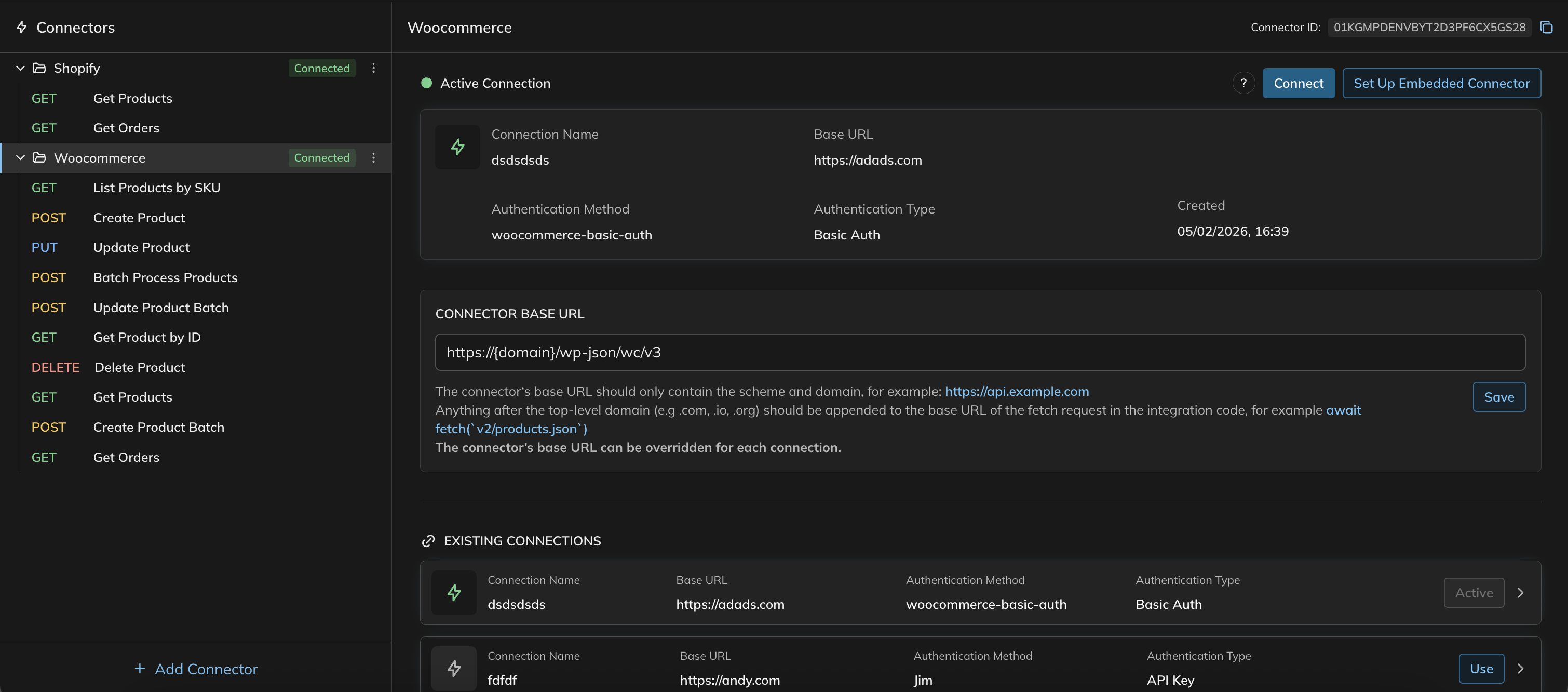
Connectors can be created two ways, through AI chat or manually via the Connector sidebar.If Connectors are created through Plan then the associated endpoints the Plan agent has detected as necessary for
the integration will be a part of the Connector and will be accseible, in the Connect tab, to test.